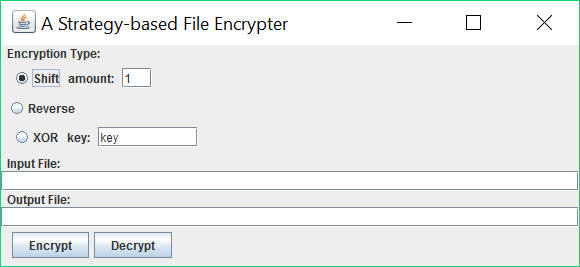
The objective of this lab is to create an application that encrypts or decrypts text files by implementing a design which employs the Strategy Pattern.
Here is a simple UI that allows a user to:

When the user presses one of the Encrypt or Decrypt buttons, each record (that is, each line) of the specified Input file is processed using the selected encryption strategy, producing the specified Output file as a result.
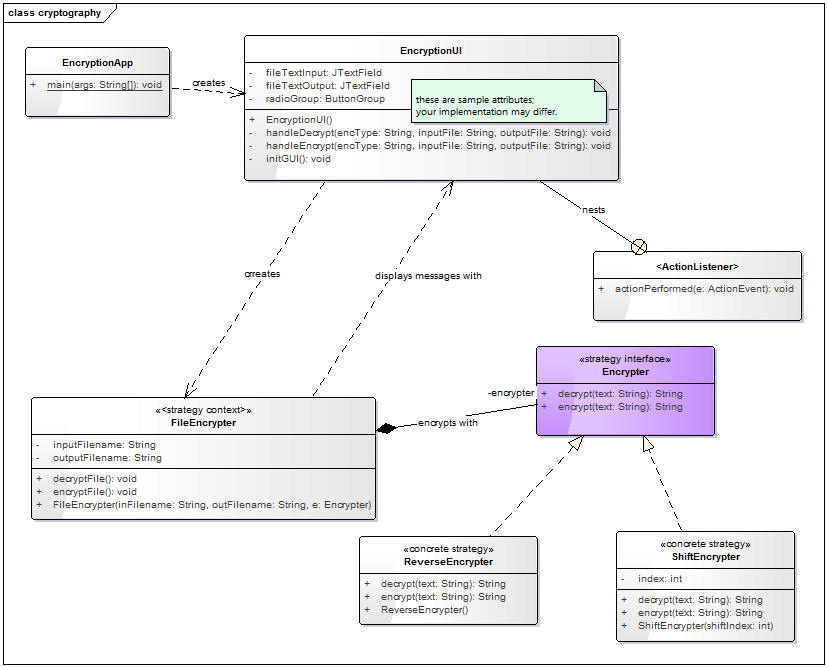
Study the following class diagram, illustrating the structure of the program:
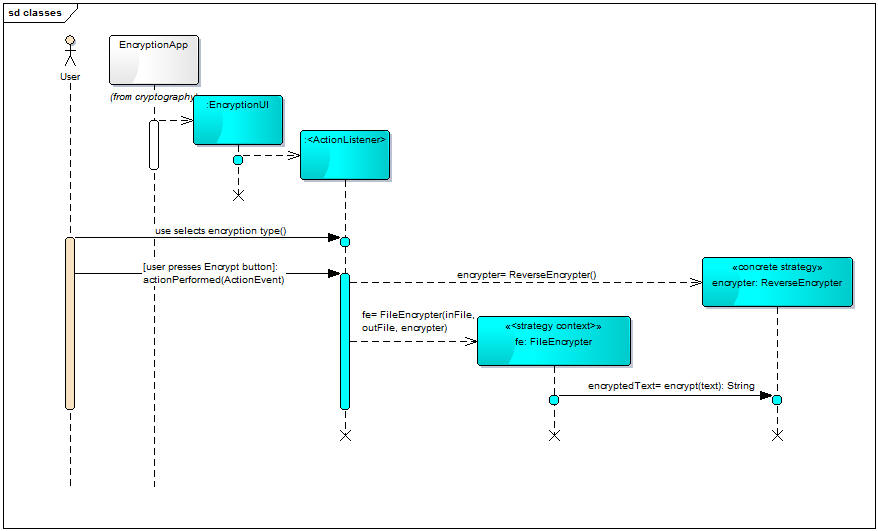
The following sequence diagram illustrates the order of operations when the user selects the Reverse radio button and presses the Encrypt pushbutton:
Your assignment is to implement this application. While you may customize your UI, you MUST implement the Strategy Design pattern substantially as shown - the key classes are FileEncrypter, ReverseEncrypter, ShiftEncrypter, XOREncrypter, and the Encrypter interface.
Note that the encryption algorithms are fairly simple (and thus not very secure compared to encryption techniques that are actually used in modern internet protocols): The ShiftEncrypter encrypts text by simply substituting the another alphabetic character for each character encountered. The index attribute (set by the ShiftEncrypter constructor) affects which character is substituted. For example, when index=1, ShiftEncrypter's encrypt() method encrypts the string Hal to Ibm, while the decrypt() method does the opposite. Similar to a Caesar cipher, if the numeric value of the character would fall outside of the ASCII range (0-255), it should "wrap around" to the other end. For example, if a code would have the numeric value of 256, it should wrap around to 0, and a numeric value of 300 should wrap around to 4. If a character falls outside of the ASCII range (0-255) before encryption or decryption, the encryptor/decryptor should raise an UnsupportedOperationException. The UI should catch the exception and report to the user that the file cannot be encrypted/decrypted.
Similarly, ReverseEncrypter encrypts simply by reversing the characters in a string to be encrypted; thus Hello there! becomes !ereht olleH.
The XorEncrypter is a little more complicated (but harder to crack): For each
character in the string to be encrypted, this encrypter does an exclusive-or (^
in Java) with each successive character in the specified key. For example, if
the key is "abc", then the encrypted string is
H^a e^b
l^c l^a o^b <sp>^c t^a
h^b e^c r^a e^b !^c, where
H^a represents the character that results from applying the exclusive-or to H
and a. Note how
the characters in the key string are cycled through. To decrypt an encrypted
string, you simply need to apply exclusive-or using the same key to the
encrypted string. Note that processing characters like this is fairly
straightforward as long as both key and the text to be encrypted are ASCII (in
which case the output is also ASCII). However, if either key or text are
non-ASCII Unicode codepoints, then the approach may have to be enhanced.
For this lab, you may assume that all input files contain only ASCII characters.
[Note that none of these approaches come even remotely close to the strength of modern encryption algorithms - but those are left to elective courses such as Network Security.]
Note that, when encrypting a file, each record of the file should not be treated as a separate String - that is, you should process the entire file contents (including newline characters). In reading and writing files, you should use Java's character-based reader and writer classes, rather than classes that deal with records (which typically strip off newline characters).
Your assignment will consist of:
When you are finished, submit your assignment according to your instructor's specific directions.
Your assignment will be automatically tested using a JUnit test framework, so be sure to implement the method signatures exactly as shown in the class diagram for the FileEncrypter, ReverseEncrypter, ShiftEncrypter, XOREncrypter, and the Encrypter classes.