This is an old version of this course, from Fall 2016. A newer version is available here.
Introduction
In this lab, you will send UDP messages between machines. You will predict the contents of the UDP message header and payload and compare it with the UDP message captured with Wireshark. You will write an informal report for this lab, and turn it in in hard-copy, perhaps even in lab.
Work this lab in teams of two, unless a different size is approved by the instructor.
Provided Materials
- Lab Checklist — I will provide a paper copy of this. You will print and submit all your materials stapled behind this checklist.
- Lab 2 Example Format
- udpclient.py - A simple UDP client
- udpserver.py - A simple UDP server
Prelab
Installing required software
- Install Wireshark, a "packet sniffer" that supports logging and analysis of network traffic.
In this course, we will use it as a tool to learn about network protocols and to find and fix problems with network applications.
- Download the Wireshark application from the web site (www.wireshark.org) and install it on your computer.
- During installation, be sure to install pcap as well
- You may find this video helpful to start exploring packets: HakTip - How to Capture Packets with Wireshark - Getting Started
- Install Python development environment
- Go to the Python Windows downloads page
- Select the latest Python release installer (e.g., Python 3.5.2). Make sure you have Python 3 (rather than Python 2 or earlier).
- On the Python release page, download an appropriate installer for your Windows environment (e.g., x86-64 for the freshman laptop).
- Invoke the installer package to install Python on your system.
- During installation, be sure to install for all users
- During installation, on the "Customize Python" page, select "Add Python 3.5 to Path" for installation. This is important for Lab 7, where you will be configuring Python.
- (You can also add the Python install directory to your system path manually using these instructions)
- Install JetBrains PyCharm (Python IDE from the maker of IntelliJ)
- (You may choose to use a different IDE if you prefer.)
- Download either the Professional or the Community Edition.
- If you choose the Professional Edition,
- If you choose the Community Edition, just install it normally.
- When creating your first project, point PyCharm at python.exe in the python folder you installed. If you used the 64 bit version of Python, this will be something like C:\Program Files\Python35\python.exe
Predicting the Contents of a UDP packet
Procedure:
- Use the figure from the text (below) to predict how many bytes each field of the header will use, and what order each of the header fields and payload message will be in.
- Make your best guess for the values of the required fields and payload data by reading through this section and the end of section "UDP Headers" below, and by looking at the client source code (also below).
- Fill in the table with these values, following the example format. (But note that the example template uses IP, which is much longer than the UDP packet you need to use.)
- Concatenate all of your bytes into a single messsage, following the example format.
- Check your work, but don't worry if you are unsure of any of the parts. You can check your answer against the real UDP packet in the lab, and it's OK if it is totally wrong, as long as you are following the process above.
- Now you are done with the prelab! Be sure to bring your prediction table and concatenated complete prediction to lab.
Read through the provided UDP client code. This code sends a four five-byte message to the server using UDP. From the code, predict the contents of the the UDP message.
In Section 3.3.2 of the text, in
6th Ed: Same section and figure, p. 202
Predict the contents of each field of the UDP header and payload data. You do not need to include any of the lower-level IP or Ethernet headers. In a table, write
- the name of the field
- the number of bytes that field uses
- the value you predict for the header in a "human readable" format (for example, as a decimal number or a string)
- the raw value of the field, written as a hexadecimal number.
You do not need to predict the value of the checksum or the source port. See the Lab 2 Example Format that illustrates the required components (using an IP header for an example). See the next section for a description of the fields used in the UDP packet.
Concatenate all of your predictions together to form a complete prediction of all the bytes in the UDP header and payload data. You can put -- or 00 for each byte that you do not predict. Just put the byte values in hex, all together without any lines separating them. For example, you might predict the bytes to be e1 15 e1 15 34 36 54 3b 6d e1 -- -- 61 62 ..., and find the actual bytes to be e1 15 e1 10 34 00 54 3b 00 01 02 6d e1 35 02 61 62 ... (This example isn't a real UDP packet — it just shows the format I want you to use for displaying your predictions). You can see an example of a complete predicted packet in the example
Describe any challenges you had or remaining questions while predicting the packet's contents. Show your prediction to the instructor at the beginning of lab.
Your predictions do not need to be perfect! As long as you make a best effort, and have a "guess" for all of the required information, you will get full credit for the prelab! Resist the urge to check your answers before lab — you will get to do this in lab.
The UDP headers
The source port and destination port fields give the port numbers of the programs on the sender and receiver, respectively. The length field specifies the length of the entire UDP packet in bytes, including both the UDP header and the payload. (It does not include the length of the lower-level headers, such as IP, and Ethernet.)
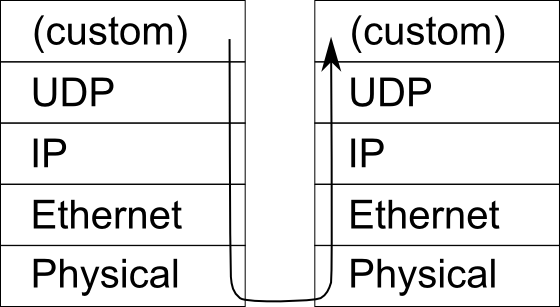
The UDP message is sent in a way similar to the envelope skit on the first day of class. Instead of HTTP at the application layer, we have just some text in ASCII. Instead of TCP, we have UDP. While TCP breakes a message into parts, UDP can only send a single (smaller) packet at a time. The only thing that UDP adds over IP is the ability to specify a port. The port specifies which program should listen to the message. How does the server know which program should listen to the message? When the program starts, it binds to that port. Then, when the server receives a UDP message, it looks up which program is bound to that port and delivers the message to that program.
Try to do conversions to hexadecimal (from ASCII or decimal) by hand as much as you can.
In-Lab
Select one of your team memberís laptops to function as the server, and another machine to function as the client.
Each student will write their own report, using the packet they captured using Wireshark on their own machine.
Student running client:
Download udpclient.py, a program that sends a UDP message. In the __author__ string, replace Phileus Fogg with your name.
In the file, replace the string server_name with the IP address of the machine you are sending the packet to (that is, the server's IP). You can find the IP address using the Windows command ipconfig. Be sure to use the IP address associated with the interface that you plan to use. For example, if you will send the packet through wireless, use the IP address listed under Wireless LAN adapter Wireless Network Connection.
Run the client program. If the server is not running, the message will simply be dropped by the server machine. This code sends a UDP message, supplied by the user, to the specified port on the server side.
Student running server:
Download udpserver.py. You don't have to enter the server's name on the server. When you leave it blank, Python will automatically listen on every interface (network connection) that the computer has. This is a very simple program that receives a UDP message. It's called a server because it will wait around for the client to ask it something. Run the server, e.g. in PyCharm. This program will remain running until it receives a UDP message. Change the server_name to the IP address of your computer. Have your partner run the client to send you a UDP message. When the message is received, the server reads the first byte to determine the number of application payload bytes. Then it displays each payload byte in hex.
Both students: Capturing the UDP Packet
Turn on Wireshark, and start capturing. Be sure to capture on the interface that you are using to send the packet. For example, if you are sending the packet through wireless, capture on the wireless interface. The Wireshark filter udp.port == 2050 may help you to find the packet. You can save your captured packets using File->Export Specified Packets. (You must stop capture with the red square before you can save any packets this way.)
In your report, include the complete actual UDP packet that was captured. Just like your prediction, show the complete captured packet with just the byte values in hex. Again, include the UDP header and payload, but not any lower-level headers. Wireshark will show you the full packet's hexadecimal, including the IP and Ethernet headers. Be sure to just pick out the UDP header and payload hexadecimal bytes.
Below your complete packet, include a table containing each field of the packet, similar to your table with the predictions. In the table, again name each field, label the field with the actual number of bytes in that field, include a human-readable value for the field, as well as the actual raw value as a hexadecimal number.
Additionally, explain all differences between your prediction and what you discover in the real packet. You can find an example of the complete actual UDP packet in hex, a table with each field, and an explanation of differences in the IP example.
Conclusions
In the conclusions section of the report, write a sentence or two describing what you (individually) learned in this lab.
Just for fun
This part of the exercise is more difficult than the remainder of the exercises. It is purely optional. Please make sure you have fully completed the required part of the lab before you start this.
You can predict the entire contents of the packet by setting the source port of the packet, and predicting the value of the checksum.
Normally, when you send a UDP packet, you do not need to specify a source port — the machine will automatically pick an arbitrary one for you. However, you can if you want to. Simply bind the client to a port on the local machine before sending the packet. In this way, you can specify what the UDP packet will be in its entirety.
The checksum is the one's complement of the one's complement sum of all the 16-bit words (pairs of bytes) in the message. When adding numbers in one's complement, you need to carry any overflow around and add it back in the one's place. (This is a result of the difference of the one's complement encoding and the two's complement encoding of a negative number.) In practice, the UDP checksum includes some fields from the IP header as well, in a "pseudoheader." See details in the text on p. 203 and consult the Wikpedia article on UDP (or RFC 768 — the standard) and/or ask your instructor for details.
Or, if you can predict all the contents of the packet, try constructing the packet and sending it in raw mode. Just make sure your program only sends one packet — in case there is something VERY wrong with it...